These are instructions on how to configure SimpleSAMLphp library on Pantheon to work with PingOne. To get started, you have to have access to PingIdentity's product called PingFederate.
In this tutorial I am going to use the same version of the SimpleSAMLphp (1.11.0) that I used in my previous blog post (highly recommended reading before you start integrating PingOne).
Requirements
- The same requirements as in ADFS and SimpleSAMLphp with Drupal.
- Access to the PingFederate product.
Install SimpleSAMLphp
See Install SimpleSAMLphp in ADFS and SimpleSAMLphp with Drupal.
Create PingOne application
You have to create an application so you can download the federation metadata file and use it to configure the SimpleSAMLphp library. To do so login to PingOne.
- Navigate to the Applications page and add a New SAML Application.
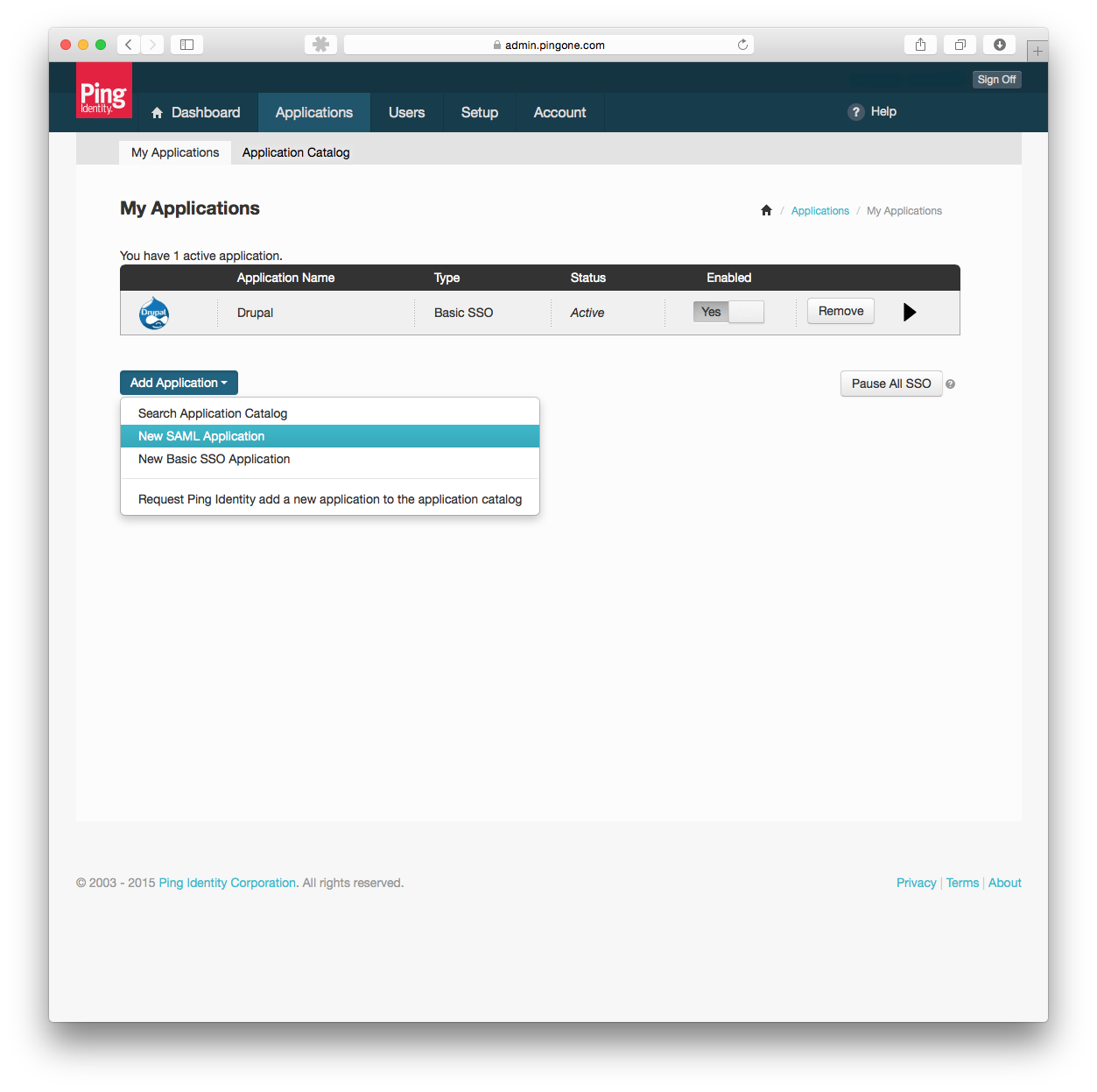
- Fill out the Application Details and press Continue to Next Step. Application name and Application description are required.
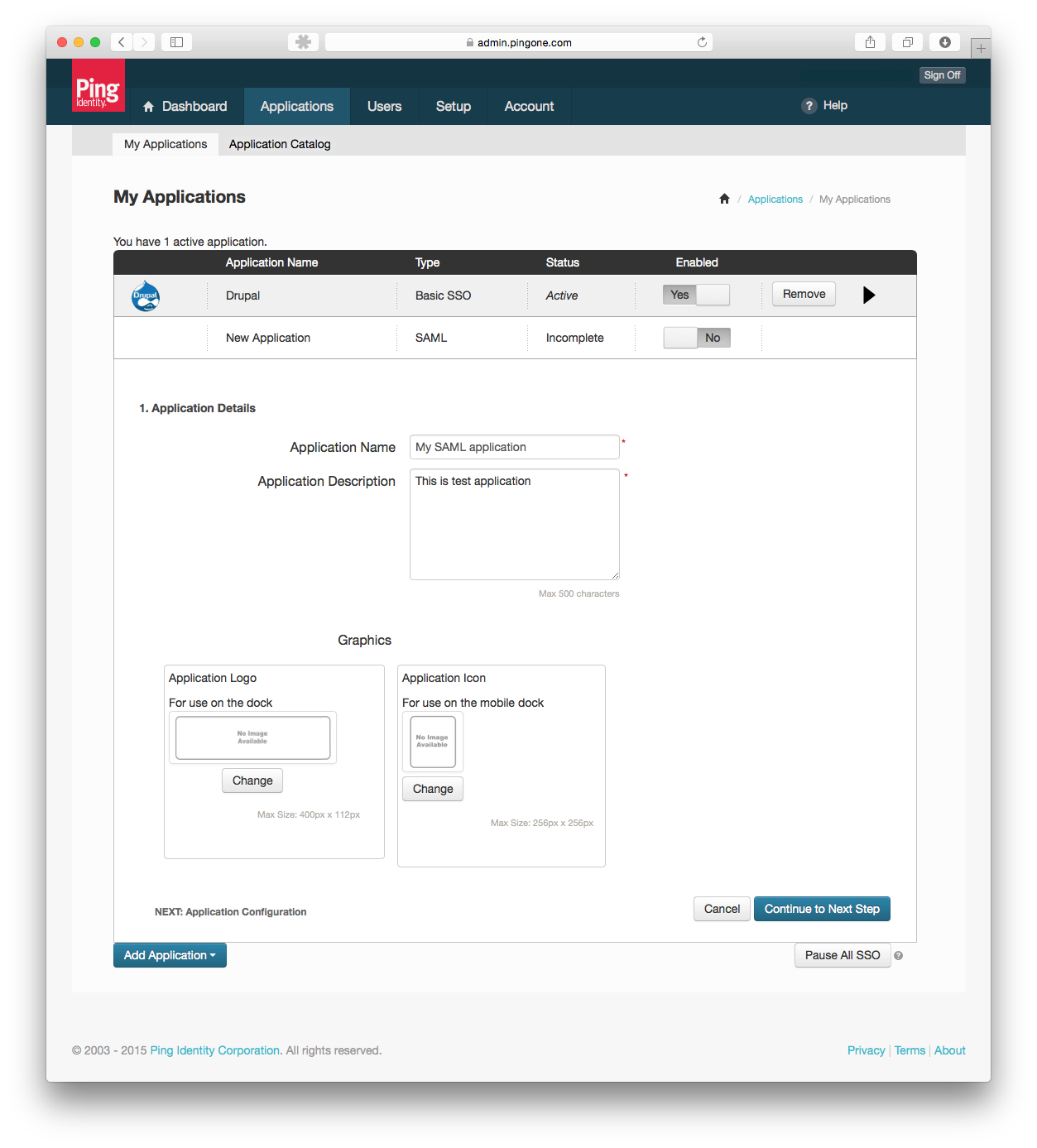
- Next you have to Download the SAML metadata and use that XML to generate configuration settings for the
/private/simplesamlphp-1.11.0/metadata/saml20-idp-remote.phpfile. Once this is done, you have to download the federation metadata file from the SimpleSAMLphp library and Upload the metadata to PingOne. The metadata uploaded will automatically populate all required fields. Make sure to upload your SHA256 certificate/private/simplesamlphp-1.11.0/cert/saml.crt. Hit Continue to Next Step.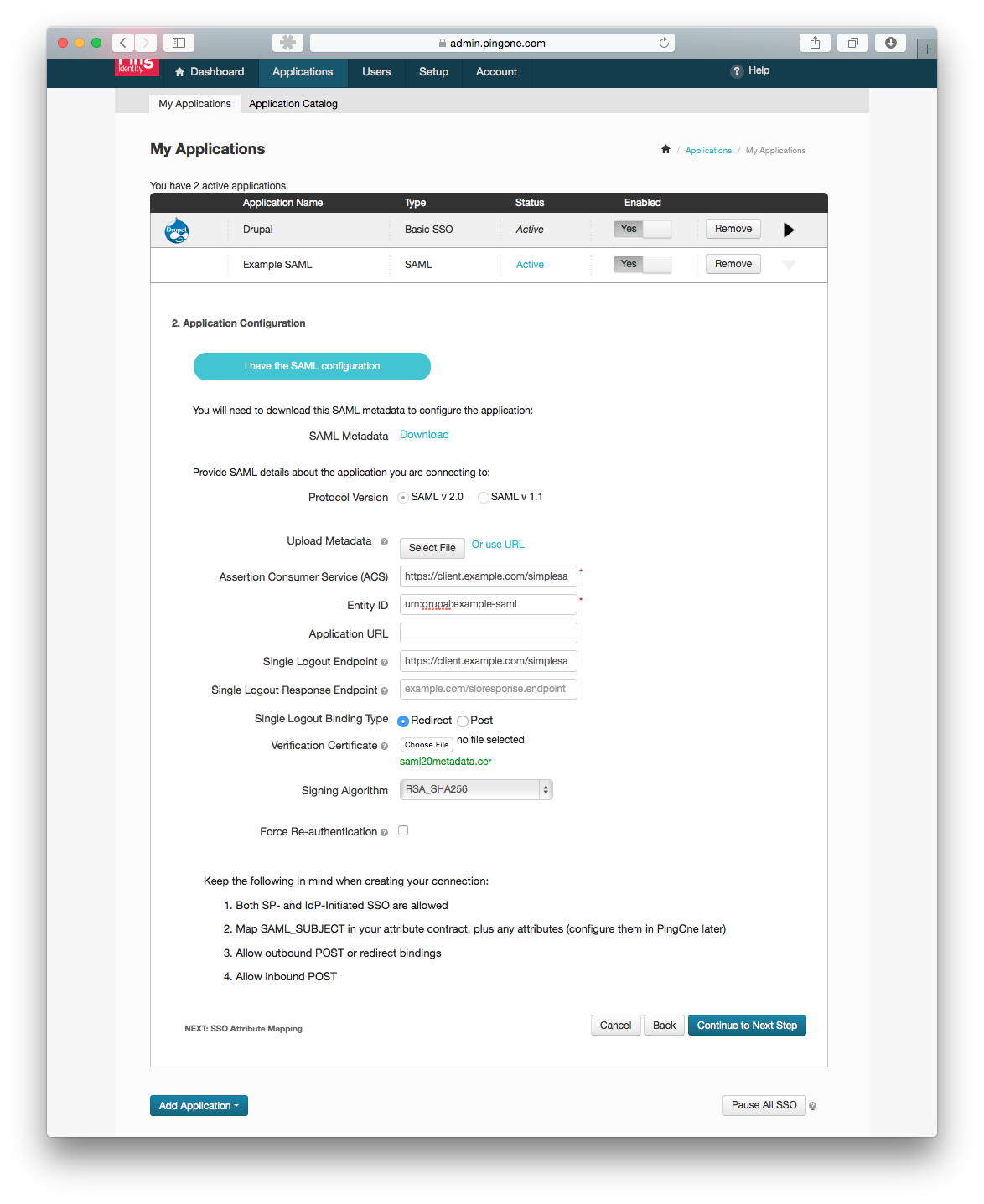
- Next configure your field mapping. This is required by the simpleSAMLphp Authentication Drupal module. The value of the Application attribute field could be anything, it doesn't have to match to my example, but make sure you use the same attribute in Drupal.
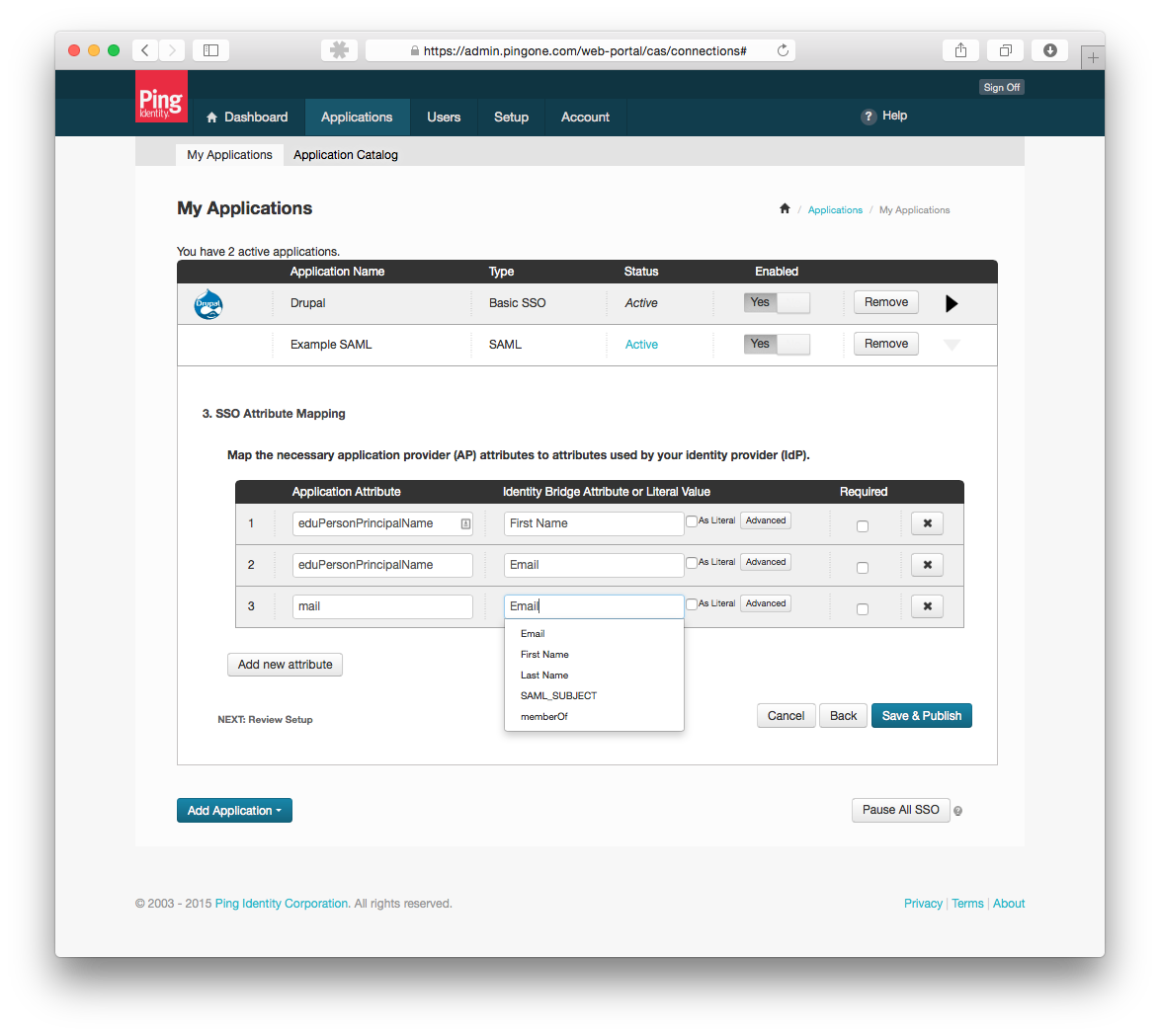
- Hit Save & Publish and you should be all set with the PingOne application.
- The last step would be Users. Create yourself a test user account so you can verify SSO works.
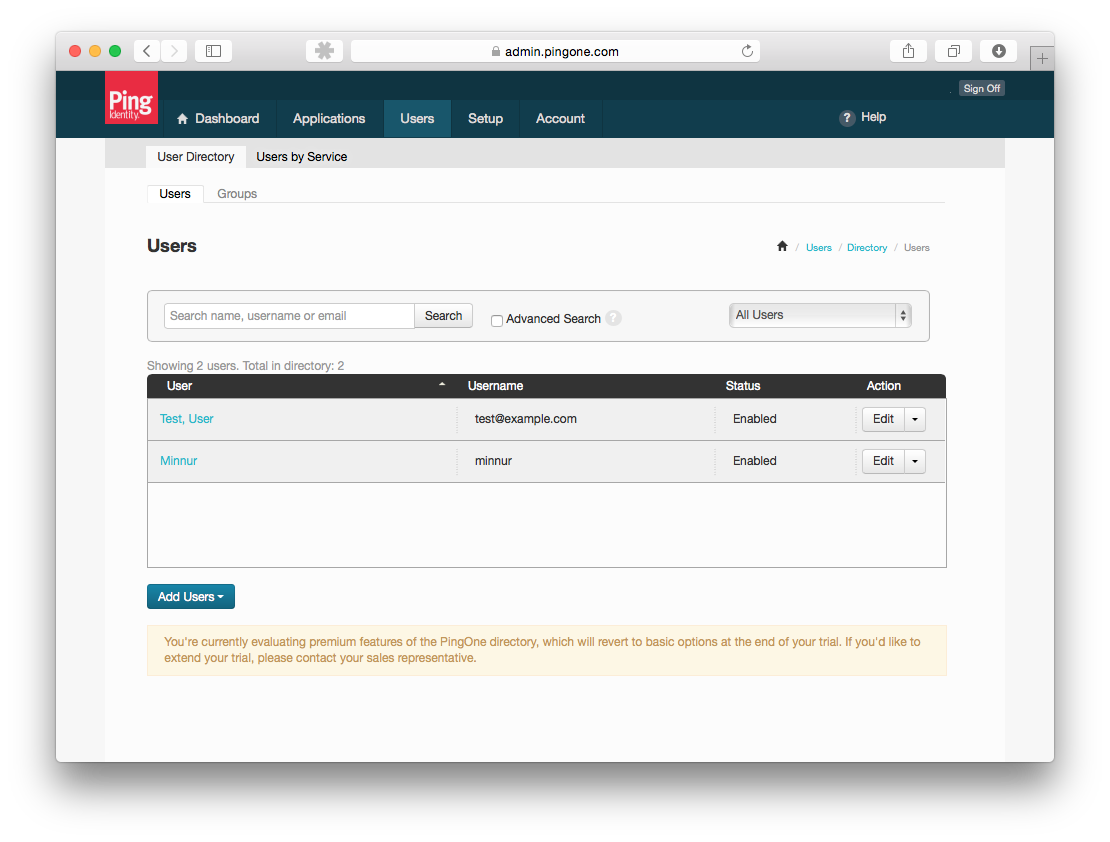
SimpleSAMLphp configuration
- To configure
/private/simplesamlphp-1.11.0/config/config.phpsee the SimpleSAMLphp configuration in ADFS and SimpleSAMLphp with Drupal. - `/private/simplesamlphp-1.11.0/config/authsources.php` looks a little bit different for the PingOne implementation. For example:
$config = array( 'admin' => array( 'core:AdminPassword', ), 'default-sp' => array( 'saml:SP', 'entityID' => 'urn:drupal:pingone-saml', // For IDP URL see your PingOne application details. 'idp' => 'https://pingone.com/idp/cd-000000000.minnuryunusov', 'NameIDPolicy' => null, 'redirect.sign' => true, // This should be FALSE. 'assertion.encryption' => false, 'sign.logout' => true, // These are the certs from `/cert` directory. 'privatekey' => 'saml.pem', 'certificate' => 'saml.crt', // Defaults to SHA1 (http://www.w3.org/2000/09/xmldsig#rsa-sha1) 'signature.algorithm' => 'http://www.w3.org/2001/04/xmldsig-more#rsa-sha256', ), );
Drupal configuration
- Follow the Basic setup from here (See Drupal Configuration section).
- User info and syncing would look as follows:
- Usually we set a username as the user's email address, if this is the case for you please try add the following:
eduPersonPrincipalName - The unique identifier for the user:
eduPersonPrincipalName - The user mail address:
mail
- Usually we set a username as the user's email address, if this is the case for you please try add the following:
Test SimpleSAMLphp and Drupal
- Try to log in, using the following URL address to test:
https://dev-example.pantheon.io/saml_login
- If you would like to support login via SAML only, replace
Login (user/login)path with/saml_login
If you have properly configured both SimpleSAMLphp and the PingOne application you should see a PingOne login screen when you login via https://dev-example.pantheon.io/saml_login. 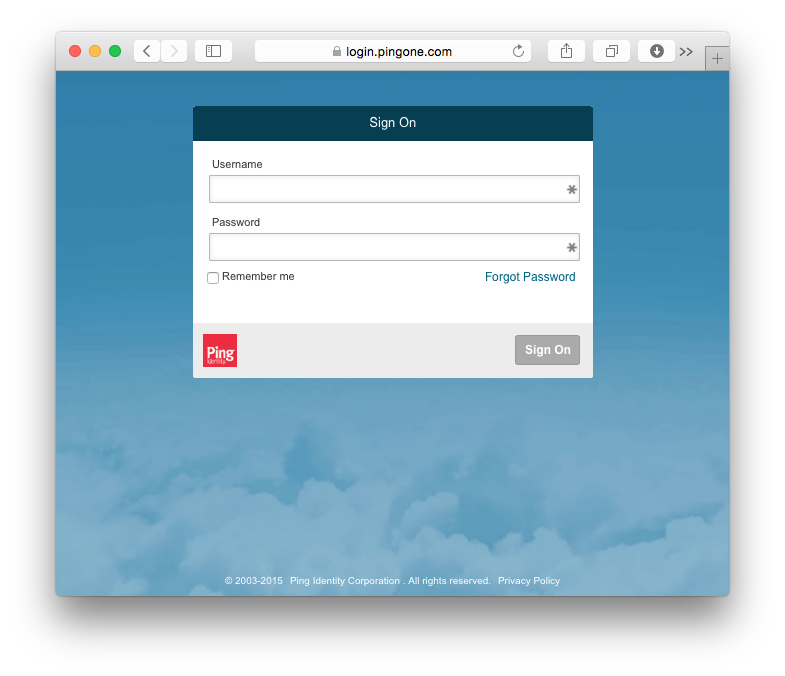
Troubleshoot
- Make sure you have correct certificates and make sure you use correct ecnryption when you generate them.
- See also the Troubleshoot section in ADFS and SimpleSAMLphp with Drupal.
Useful links
- Drupal 8 Module of the Week: simpleSAMLphp Authentication
- More useful links
- Additional links